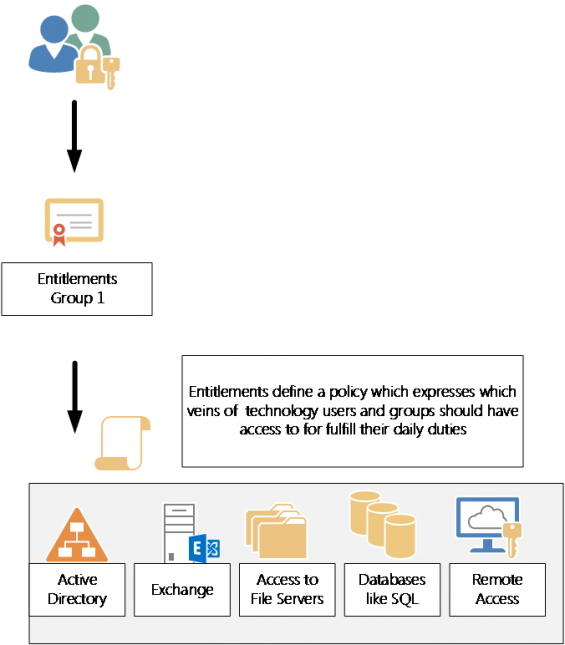
One of the common questions that arises in the IT industry today, what is Identity Management? Identity Management (IDM) is having governance or policy over who has access to what information out of your existing users. The old way of giving users within your environment access to certain servers, files, etc. was on an as-need and individual basis. Applying governance on an individual basis meant an IT resource would manually have to provision rights for users. As technologies in companies swell, the likelihood of mistakes using a manual process would only increase with time. This is not only time consuming, but hard to manage. It also introduced points of vulnerability in guaranteeing compliance with standards such as HIPPA, Sarbanes Oxley and so on.