
In the world of virtualization, there are many inherent security features that come with a virtual environment natively, but with the rise of Software Defined Networking (SDN), we have a new layer of security which can be easily added to any virtual environment. SDN strips away the traditional boundaries of IT security and brings them directly to the guest virtual machine. Through a concept referred to as Micro Segmentation, a central next generation firewall policy can be defined at the interface level of the virtual machine, effectively plugging each server in your environment directly into a firewall, providing protection, both inbound and outbound for all traffic to and from that host.
And unlike operating system (OS) level firewalls, these firewalls bring to the table the full feature set that we are used to at our perimeter. When one can bring that level of security that our organizations choose deploy to protect our entire organization and deploy that same level of protection to each server in our virtual environment, it should be considered a win for any organization because we are protecting our most valuable asset, our data.
Hardware Defined Networking vs Software Defined Networking
First, an overview of what SDN really is. Hardware defining networking (or traditional networking) is made up of switches, routers, firewalls, load balancers, vpn concentrators, and so on. These are all the items that every network administrator has been working with since the dawn of modern computing. A traditional environment looks something like this:
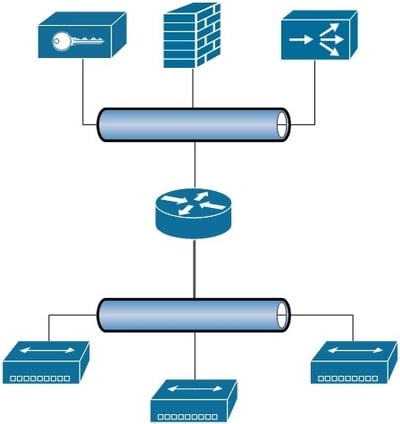
Where the edge of your network is connected to another network (often the internet) and various services are deployed for permitting or denying access to your internal resources, firewalls, vpn concentrators, load balancers, etc. Those are often connected to a router of some form, either a traditional router or a multilayer switch, which then is connected to the internal network, distributing out to various access layer devices to connect to your internal physical resources. All of these devices are connected by the most common differentiator between hardware networking and software networking, cables.
SDN is fundamentally performing all the same resources inside the virtual environment. In the same manner as with virtual servers, the hypervisor manages the resources of the guest operating systems and interconnection between them, effectively creating this:
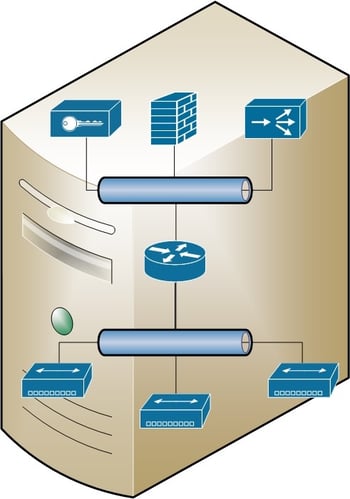
Within your virtual environment, SDN can provide all the same services you would expect from a physical network, just without the cables. Now, you will need cables to connect the servers to each other via a switch or two and there will be some components of the traditional networking that will still need to be in place to connect your virtual environment to your physical, but many of those components can be functionally simplified to only provide services required for your physical hosts and no longer require the extension into the virtual environment and potentially gain some performance in the process.
With SDN, the need for the data to leave the virtual host to go from one guest to the other is removed. If the guests are on different network segments within the same host, the traffic can be routed at the hypervisor of that host and doesn’t need to exit the host on the wire, be routed, and return to that host. Freeing up network bandwidth in and out of your virtual hosts as well as a small amount of network latency inherent with a router hop.
Also, most SDN stacks provide fundamental services to perform IPSec VPN termination, Layer 3 and 4 firewalling and load balancing, as well as, support for dynamic routing protocols. This can reduce network complexity of external services and integrate the fundamental features of the network directly into your hypervisor, reducing network sprawl. If the more advanced services for these network components are required, there are many 3rd party virtual appliances that can be deployed within your virtual environment to provide Layer 7 firewall inspection services, intrusion prevention, web application firewalls and many more.
With all virtual services, there is a blend of physical hardware with virtual technologies. Unlike the original design or philosophy behind virtualization of a company’s server hardware, virtual networking has come into play to facilitate the virtualization of the guests that reside on your virtualization targets. Due to the quantity of servers and services that are being virtualized, it made sense to bring the networking components closer to the core of the operating system. And by eliminating what has traditionally been the bottleneck (the speed of the network), server to server transactions can take place at the kernel of the hypervisor allowing for sub-millisecond response time, without changing IP addresses or modifying the applications in anyway.
Communication between different hosts where SDN has been enabled requires a simple configuration of the hardware switches to configure what is known as an overlay network, almost a network on the current network, or building a virtual network over the current hardware network. Creating something similar to this:
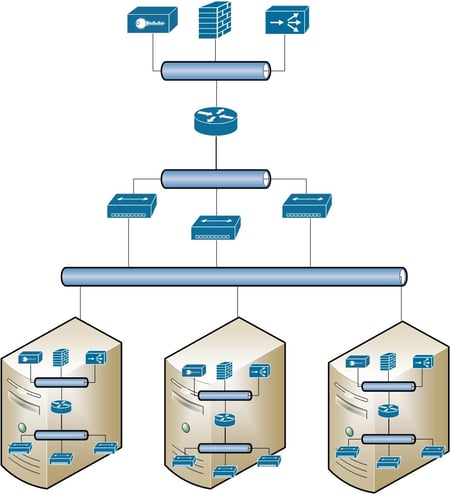
Software defined networking, at its core, is taking all the features that have traditional been in purpose built hardware and deploying them as software on top of our virtual servers. In the end, this can assist with ease of management and simplification of a datacenter environment by putting the network resources where they need to be and leaving out the need to ‘run a cable’ and allows for the same scalability that virtual servers provide for the enterprise. Need another load balancer? Deploy another software image into the environment, no additional hardware needed. Need to update the firewall rules for the 10 additional web servers that were just deployed? Add them to the group with the existing web servers, the firewall rules will update when the group gets modified.
Security Benefits of Software Defined Networking
Security appliances in a traditional network design are often put at choke points within the network. Areas in the network where a transition from one LAN to another LAN would occur. Generally deployed at the boundary for the internet, often deployed at the boundary for the WAN, but hardly ever at the boundary between the user network and the server network.
Why is that? The most common reasons are:
- The bandwidth requirements between the users and the servers is high and a hardware based security appliance to handle that need is very expensive
- The users are on the same network or vlan as the server, which does not provide for a choke point to install any type of hardware appliance
Those two reasons are what most commonly prevent adding additional security to the server environment, but with the addition of software defined networking to the virtual environment, both of those concerns can be eliminated. Most software defined security virtual appliances deploy their services at the virtual network interface to the server (vNIC), and security policies can be applied directly at the vNIC, reducing the bulk bandwidth requirements of all the servers and only requiring that single server’s worth of bandwidth to be monitored. And, because it is deployed at the vNIC level, the polices applied are bound to the specific server, regardless of its current IP address. So, the server and the clients can be on the same network, but the security policy is still being applied to the server without needing the choke point in place. This is called micro-segmentation.
Micro-segmentation can occur between both the client-server transactions and the server-to-server transactions occurring within the environment. There are some added benefits to micro-segmentation beyond what has been listed above, including providing, for example, protections for web servers from each other within the same network. Traditionally, dmz’s were put in place to isolate servers by function, but this didn’t protect the servers if another server on the same network was compromised. With micro-segmentation, those servers can be limited to exactly which IP addresses they can communicate to prevent lateral movement within a network.
SDN security also has the ability to authenticate users when they access a server over the network, before the server even challenges them for a login, seamlessly, in the background without the users even being aware this level of security is in place. Restricting access to an organizations sensitive financial or human resources applications to only the users in those groups and enforcing the need to know at the network level and not relying on server security to be in place and to prevent password-guessing as this challenge is performed at the network level and not at a user login screen.
SDN security also has all the features expected of a virtual environment, including scalability and automation. As more virtual hosts are brought online, security features are duplicated those hosts and all the features can be scripted through automation tools, allowing virtual servers to be spun up and the firewall rules be already defined, not requiring an additional change after the server is online and providing security immediately as the host is being built and secured.
Conclusion
Deploying a software defined network within a virtual environment has long standing benefits to any server farm, from initial deployment to decommissioning and all the way through the life-cycle of the application being deployed. Being able to rapidly deploy new networks with the virtual guests and providing a security at each step of the process.




Comments