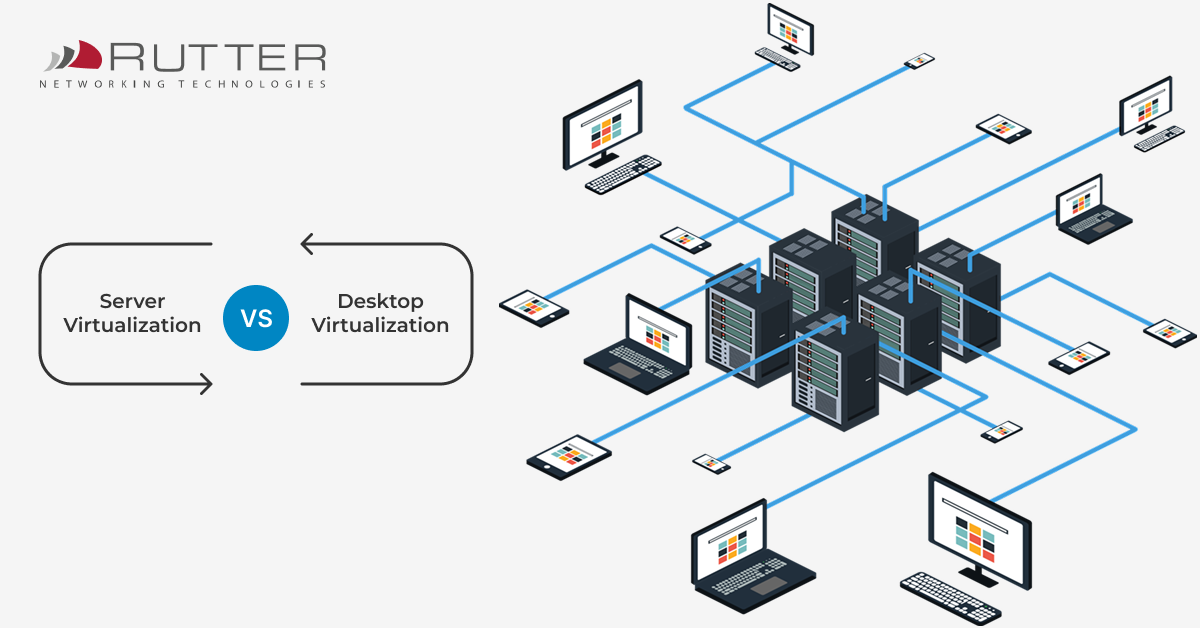
Virtualization has transformed the way businesses manage their IT infrastructure. By creating virtual environments, companies can reduce costs, improve flexibility, and enhance data security. However, when it comes to choosing between server virtualization and desktop virtualization, many decision-makers struggle to find the right fit.