
From a Microsoft Azure Active Directory perspective, there are two approaches to MFA:
1. A laser accurate approach specific to the application in the Azure blade using conditional access
2. A global approach managed through the “Multi-factor authentication” page via Office 365
Let’s examine the first option. This version is part of an Office 365 subscription. At first glance, this is leveraging a feature set that is already paid for. However, once a user is enrolled and needs to get another token for an application, such as Outlook 2016, they will face multi-factor authentication. Recently, Microsoft updated the refresh token lifetime to 90 days, as stated in this article.
This raises a few acceptance questions:
- Is it suitable that Outlook 2016 users who show at the main office need to enter a 2FA verification periodically?
- Does the company enforce compliance of ActiveSync and other non-Outlook mail clients? Newer versions of ActiveSync licenses by Apple now supports OATH as of IOS 10. If any users have ActiveSync clients who still use basic authentication, they would need to use “app passwords.”
Contrary to this, there is the conditional access approach. For example, if a company elects to challenge Outlook 2016 sessions when users are in flight, 2FA can be imposed. This version of conditional access requires at least Azure AD Premium 1 licensing. Not only can this MFA be specific to office location (by public IP) but also application consumption for Office 365. In image 1 below, a policy can be seen to just including “modern authentication clients” and browsers but exclude ActiveSync (as a means to avoid app password entanglements).
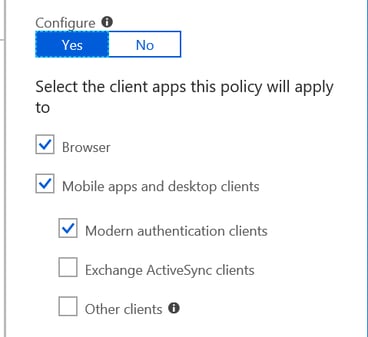
Image 1
Things worthwhile to note, as of 6/25/18 Microsoft has announced to make MFA a "baseline policy" for all organizations with Azure AD account administrators.
“The preview can currently be accessed within the Azure Portal by going to the Conditional Access blade. There is an option in there to turn on the baseline policy and "Require MFA for administrators." The interface lets organizations specify which Azure AD administrators will be subject to using MFA. The options include:
- Global administrator
- SharePoint administrator
- Exchange administrator
- Conditional access administrator
- Security administrator
While this feature is currently at the preview stage and it's optional to try, Microsoft plans make it a default setting for organizations when it's deemed to be at the "general availability" (or production-ready) stage”
This is shown in Image 2 and 3 below. Microsoft does not intend to charge Global admins, but other admin tiers would need some flavor of Azure AD subscription to leverage this.
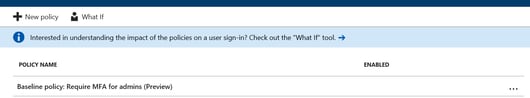
Image 2
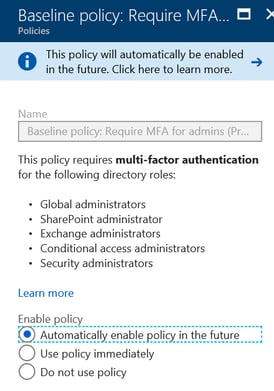
Image 3





Comments