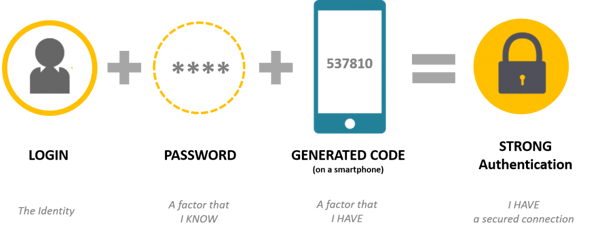
Two Factor Authentication (2FA) or Multi-factor Authentication (MFA) is the most common preventative measure that companies and organizations implement as an additional layer of security to the standard username and password login credentials on a website or application. Taking a half-step back, 2FA/MFA can be described as something you know and something you have. 2FA/MFA is currently used on almost every application, from banking websites to SaaS services to video games
The most common question I get is ‘what should I use for Two Factor Authentication?’.
Years ago, the answer was rather simple, as there was only one player in this space. It was RSA tokens or nothing. That market has changed dramatically. There are many options available for 2FA, and the choices seem almost daunting. In this blog post, I will be walking you through your options and hopefully provide some guidance on this path.
I've broken this down into three options. 2FA solutions that you would buy; for example, RSA or Duo authentication. 2FA solutions that you would borrow; such as Microsoft's Authenticator for Office 365. And lastly, 2FA solutions that you would loot (get for free), like Google Authenticator.
Loot

I'll start with the free options because everyone likes free, don't they? Google has a free application for most smartphones that can integrate into a lot of websites and current services available. It's rather simple to set up on the client side, generally scanning a QR code on a website or from an email to make it work successfully. Free is good, right? The challenge with free is that if you are looking to deploy this for an internal application or developed SaaS application, it would require your developers to integrate Google's code into your website and to depend on the application. This might be the more considerable challenge that it would seem on the surface.
Borrow

There are many services available now that have a 2FA solution build into them. I say ‘borrow’ because more often than not, you are already paying for them as part of another service you are getting. Microsoft’s Office 365 suite (including Exchange online and Sharepoint) have various options already built in for 2FA. The Microsoft Authenticator is my personal preference, once again, another smartphone application that will send you a push notification to authorize a login to one of their services. They also offer everything from a callback option (yes, they call your phone, and you need to hit the pound key to log in), to SMS messages with a pin included, to even an email verification. The Authenticator application is the least disruptive, in my opinion, and doesn't always require cell service because it will use a data connection as well. (Besides, we get enough text messages and phone calls as it is, don't we?)
Buy
 Capital expense! (Say it with me, ewww…) Most companies will often look for the one ring to rule them all. They want a solution that is going to accommodate all their options so that users only have one application they need to load on their smartphone that will work for everything. As I previously mentioned, RSA was the key player in this space for a long time. Dating back to using credit card style tokens with a pin code on them, now offering a smartphone application that can even support multiple users. They are not the only option in this space anymore. They still probably have the most extensive adoption of the off the shelf style solution, but there are others in this space as well. Duo has become a personal favorite as an alternative. Lower initial cost and a lower overall cost of ownership. Also, offering integrations beyond a smartphone application, including smart cards and certificates which can integrate into their solution. These can give you the option to authenticate the user and the machine, most often used if you only want a corporate asset to connect to a remote access VPN for example.
Capital expense! (Say it with me, ewww…) Most companies will often look for the one ring to rule them all. They want a solution that is going to accommodate all their options so that users only have one application they need to load on their smartphone that will work for everything. As I previously mentioned, RSA was the key player in this space for a long time. Dating back to using credit card style tokens with a pin code on them, now offering a smartphone application that can even support multiple users. They are not the only option in this space anymore. They still probably have the most extensive adoption of the off the shelf style solution, but there are others in this space as well. Duo has become a personal favorite as an alternative. Lower initial cost and a lower overall cost of ownership. Also, offering integrations beyond a smartphone application, including smart cards and certificates which can integrate into their solution. These can give you the option to authenticate the user and the machine, most often used if you only want a corporate asset to connect to a remote access VPN for example.
Options, options, options
There are many options available. As you have probably seen, I said smartphone about a half dozen times. Every solution has a smartphone application. My recommendation, just get over it. Yes, people can lose their phones, but every solution provides a relatively simple option to reset a device one the app is loaded again. Moreover, most people guard their smartphones as if it were one of their most sacred possessions. The cost of ‘soft tokens' is often far less, or free!
Also, abandon the idea of using a single 2FA for everything. Currently, I have a tab on my phone that is just MFA soft tokens. One for AWS, one for Azure and Office 354, one for remote access VPN, and the list goes on. Of course, the more that you can use a single 2FA solution for, the better. However, at the end of the day, nothing is going to work seamlessly with every application. Standardizing as much as possible helps, but with the development of many SaaS applications, you are most likely going to be tied to whatever solution they support. Don't fight it, roll with it. The best way to look at it is to accept, like for every website, you have a different login (username/email address/password), you are most likely going to have a different 2FA solution for it. The real recommendation here would be to deploy one 2FA for internal resources (Like Duo) and use it for as much as you possibly can, then use the integrated solution for SaaS/PaaS/IaaS solutions.
Pin, push or call
As each of these solutions offers multiple ways to validate that you are indeed you, there are some that are better than others. The traditional callback option should go the way of the Dodo and stay in the 1980s like monochrome monitors. The real options now should be a pin code or a push notification. Google, Microsoft, and RSA all provide options for a pin code, and this is the most common type of 2FA on the market. You can log in, then type in a pin that appears on your smartphone, or one that is sent to you via an SMS message. The new wave is done via push notification to an application on your phone. Microsoft and Duo (at least) provide this feature. When you log in to a site, server or service, a notification is sent to your smartphone for you to accept the login then. No pin required. Just hit ‘yes' or ‘accept' on your phone to process the login. There are some tremendous benefits to this. For one, it doesn't require you to have cell services (like an SMS) because it can use data. Second, there is little to no chance of the pin expiring on your phone in the middle of your login, resulting in a failed login and having to start over.
The Finale
There are many options available for Two Factor and Multifactor authentication on the market. Now it’s a matter of choosing what’s right for your specific business needs. With these options laid you in front of you, I hope that this provided some guidance on where you can go with the solution. If you have further questions, feel free to reach out to us. We will be able to guide you down the right path for your organization.



Comments