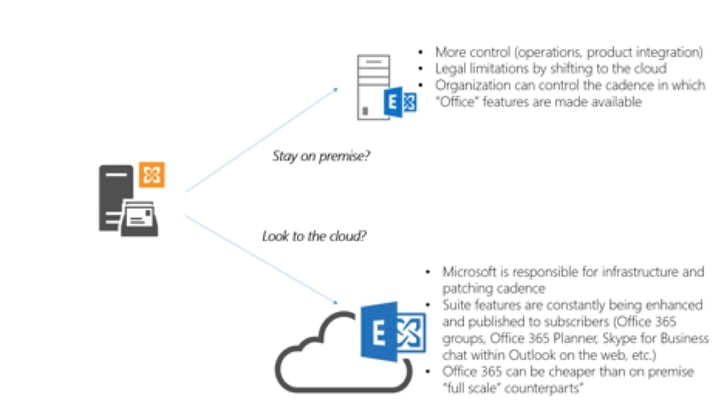
 With Exchange 2010 now in extended support, many companies are in are in the fork in the road in determining their Office 365 trajectory. Common considerations are shown in the diagram above.
With Exchange 2010 now in extended support, many companies are in are in the fork in the road in determining their Office 365 trajectory. Common considerations are shown in the diagram above.
So with the strides that Microsoft has made for the cloud, why aren’t all companies automatically going to the cloud? Based on client feedback, here are reasons why some of our clients have either “thinned” their Office 365 portfolio or delayed entry into the Microsoft cloud all together:
- Backups. For Exchange Online, a mailbox is configured to retain deleted items for 14 days, by default. You can use the Exchange Management Shell to change this setting to a maximum of 30 days. Though hold policies can be used to extend matters; you cannot call Microsoft have them rehydrate deleted mailbox content after it was deleted 6 months ago. For SharePoint Online, all items are automatically deleted approximately 90 days after they were originally recycled. Depending on the company these limits may or may not be acceptable. To fill this, gap an ecosystem of backup products have started to emerge in the market place.
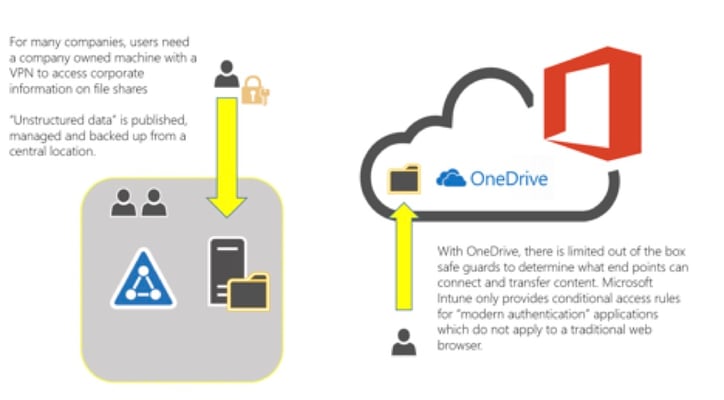
- Conditional Access to data. According to an April 2016, survey of Gartner, the second most popular Office 365 application is OneDrive. For users this is 1 TB of storage at their fingertips. For administrative and security admins, this is an instance cause of concern. As shown in the diagram below, non-corporate machines can access this data out of the box and from across the globe:
Though Microsoft does offer MDM conditional access control to “modern authentication” applications; these safe guards are not applicable to modern browsers. To ensure that cloud data can only be accessed from the domain joined machines and sanctioned registered devices, bolt on solutions like Netskope (a cloud security broker) are gaining in popularity in the market place.
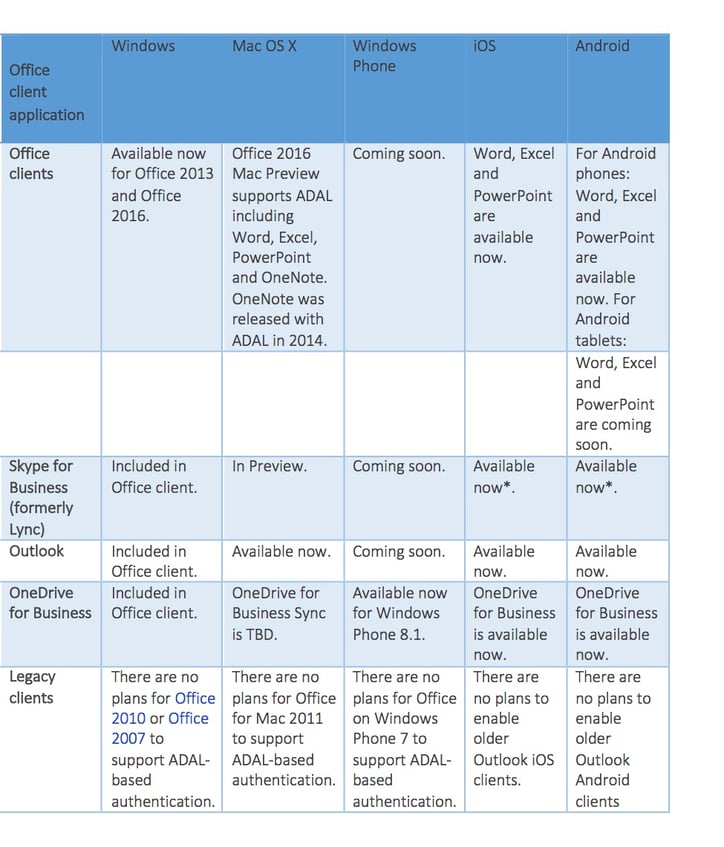
Sign on experience. Active Directory Authentication Library (ADAL), or what is being termed as “modern authentication”. Prior to ADAL based authentication, the Office 2013 client sign in flow (using the Microsoft Online Sign-In Assistant) required the WS-Trust protocol for users to sign in. So even with an ADFS deployment, an on premise user was prompted to enter and save their credentials until their password expired. With ADAL, enabled in the Office client, we no longer rely on using basic authentication for the Outlook. However, as the table below shows, mileage of this experience will vary based on the version of Outlook being used:
Conclusion:
So clients looking to explore Office 365 need to determine with their directory & messaging consultants:
- The sign in experience the desire (SSO or same sign on)?
- If SSO, consideration for ADFS especially with Windows Server 2016 on the horizon. To read more about conditional access control within the future release of ADFS, please refer to: https://technet.microsoft.com/en-US/library/mt617220.aspx
- What effort is needed to get end point clients aligned with the goals of the cloud (Office upgrade, registry scripting, Outlook CALs, etc.)?
- What the sign on experience should be for machines whom are domain members but are outside the corporate network?
- Windows 7 vs Windows 10 (Azure joined machines with device registration).
In the next chapter we will look at other points of consideration before adopting Office 365





Comments