
Historically, one of the challenges of Azure was trying to contain private traffic to resources such as platform-as-a-service (PaaS), Azure files, and Azure SQL. Customers envisioned having a cloud data center with services, and they strived for a vehicle to encapsulate the traffic as they would with a traditional data center.
The only option administrators had was to use service endpoints. Service endpoints were Microsoft’s first efforts to lock down traffic flow by “[enabling] private IP addresses in the VNet to reach the endpoint of an Azure service without needing a public IP address on the VNet.”
Though these efforts were a step in the right direction, service endpoints still face fundamental issues:
- Traffic to your PaaS would still be leaving your virtual network
- Your Azure PaaS resource is still accessible from the internet
The new standard to remediate this issue is the introduction of private endpoints. According to Microsoft, Azure Private Endpoint is a network interface that connects you privately and securely to a service powered by Azure Private Link. A private endpoint uses a private IP address from your VNet, effectively bringing the service into your VNet.
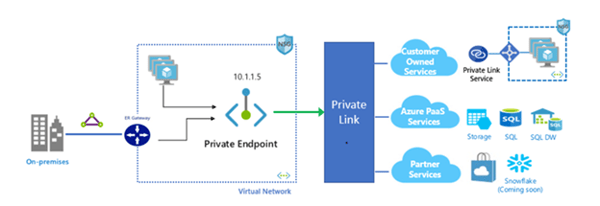 With this private network interface (NIC) on your VNet, traffic will pass through a private link to your PaaS environment. This eliminates the need for:
With this private network interface (NIC) on your VNet, traffic will pass through a private link to your PaaS environment. This eliminates the need for:
- Gateways
- Network address translation (NAT) devices
- Public IPs
Below is a list of all platforms as a service that can use private links:
|
Private Link Resource Name |
Resource Type |
Subresources |
|
Private Link Service (Your own service) |
Microsoft.Network/privateLinkServices |
empty |
|
Azure SQL Database |
Microsoft.Sql/servers |
SQL Server (sqlServer) |
|
Azure Synapse Analytics |
Microsoft.Sql/servers |
SQL Server (sqlServer) |
|
Azure Storage |
Microsoft.Storage/storageAccounts |
Blob (blob, blob_secondary) Table (table, table_secondary) Queue (queue, queue_secondary) File (file, file_secondary) Web (web, web_secondary) |
|
Azure Data Lake Storage Gen2 |
Microsoft.Storage/storageAccounts |
Blob (blob, blob_secondary) Data Lake File System Gen2 (dfs, dfs_secondary) |
|
Azure Cosmos DB |
Microsoft.AzureCosmosDB/databaseAccounts |
SQL, MongoDB, Cassandra, Gremlin, Table |
|
Azure Database for PostgreSQL -Single server |
Microsoft.DBforPostgreSQL/servers |
postgresqlServer |
|
Azure Database for MySQL |
Microsoft.DBforMySQL/servers |
mysqlServer |
|
Azure Database for MariaDB |
Microsoft.DBforMariaDB/servers |
mariadbServer |
|
Azure IoT Hub |
Microsoft.Devices/IotHubs |
iotHub |
|
Azure Key Vault |
Microsoft.KeyVault/vaults |
vault |
|
Azure Kubernetes Service - Kubernetes API |
Microsoft.ContainerService/managedClusters |
managedCluster |
|
Azure Search |
Microsoft.Search/searchService |
searchService |
|
Azure Container Registry |
Microsoft.ContainerRegistry/registries |
registry |
|
Azure App Configuration |
Microsoft.Appconfiguration/configurationStores |
configurationStore |
|
Azure Backup |
Microsoft.RecoveryServices/vaults |
vault |
|
Azure Event Hub |
Microsoft.EventHub/namespaces |
namespace |
|
Azure Service Bus |
Microsoft.ServiceBus/namespaces |
namespace |
|
Azure Relay |
Microsoft.Relay/namespaces |
namespace |
|
Azure Event Grid |
Microsoft.EventGrid/topics |
topic |
|
Azure Event Grid |
Microsoft.EventGrid/domains |
domain |
|
Azure WebApps |
Microsoft.Web/sites |
site |
|
Azure Machine Learning |
Microsoft.MachineLearningServices/workspaces |
workspace |
Other advantages of private endpoints that should be noted:
- Hybrid environments with express routes and VPNs can leverage private endpoints to contain sensitive traffic within your cloud and on-premise data centers.
- There is inherent protection against data leakage because you are mapping directly to your specific resource rather than to the service.




Comments