
Recently, one of our clients expressed concern because they noticed that personal information was showing on users’ profile cards in Office 365. This information included users’ home addresses and personal phone numbers, among other information.
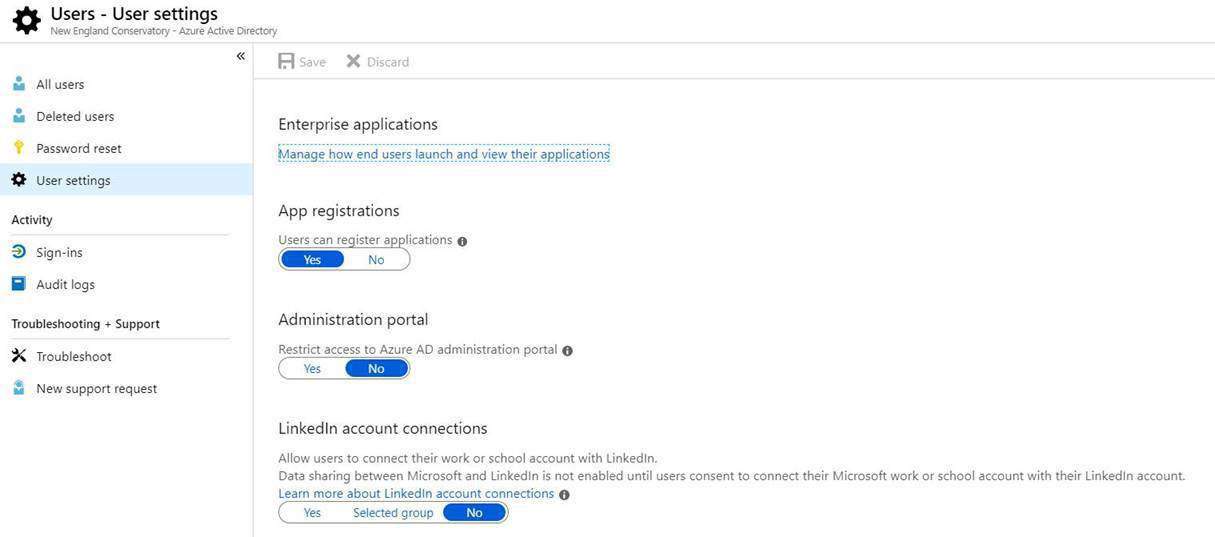
After our team checked Microsoft Exchange, the Global Address Book, and Office 365, we were convinced that this information was not coming from inside Microsoft’s email system. What we discovered, however, was that Office 365 allows a default connection to a user’s LinkedIn account, which can contain personal information. This information is then able to sync to the Office 365 Profile Card.
LinkedIn Support details this default connection further: When you create a LinkedIn profile, certain areas of your LinkedIn profile can be set to be viewed publicly—meaning this public profile can be viewed if a person visits your profile through a public search engine or through a third-party email service such as Outlook, Yahoo, or Samsung’s mobile email application.
LinkedIn users do have the ability to adjust the visibility settings of their public profile to only show information they are comfortable sharing publicly. It should be noted, however, that once changes are made to a public LinkedIn profile, it could take up to several weeks for the information to correctly show in search engine results.
If you are a global administrator in your organization’s Azure instance, you have the ability to control access in the Azure tenant. Initially, access to LinkedIn public profiles is allowed by default, but you have the ability to turn off access or restrict access to certain uses who are members of a group.
Our team of industry experts is always looking to help answer our clients’ questions and to be proactive in monitoring any potential issues.




Comments