Picture this, you have an employee traveling internationally for a work event, but they forgot their password and are unable to get in touch with the IT department. As a result, they can’t get into the programs and platforms needed to accomplish what they set out to at the event. Situations like this are becoming more and more common due to the continued increase in popularity of remote and hybrid workforces.
IT is supposed to help increase user productivity, not hinder it. So how could IT improve user productivity in a situation such as the one previously mentioned? Two words: Passwordless Authentication.
I know what you may be thinking. “How would this increase user productivity? We always have IT staff on call for situations like this”. Well, Passwordless Authentication increases productivity for users by removing the burden of memorizing long, complex password combinations and from having to constantly reach out to their IT department to have their passwords manually reset. Not only will the user trying to get to that event be more productive, the IT department will as well.
Resetting a password may seem like a simple task, but it still costs organizations time and resources. Studies have found that between 20%-50% of all IT help desk calls are for password resets and range from 2-30 minutes to fix. In a US-based survey, 37% of the users reported having more than 50 password resets in a single year. As managed services providers, our engineers at Rutter Networking Technologies have recognized Passwordless Authentication as an easy way to increase productivity across the board and empower the hybrid workforce by ensuring their work content is secure.
What is passwordless authentication?
Passwordless authentication refers to the process of verifying a user's identity without requiring a password. It replaces the traditional method of using a combination of a username and a password to access an account or a system. Instead, passwordless authentication uses alternative methods such as biometric authentication (such as fingerprint or face recognition), one-time passwords (OTP) delivered via email or text message, or hardware tokens.
What are the drawbacks of basic authentication?
Most organizations have protocols in place outside of usernames and passwords via HTTP basic authentication, but it bears highlighting the drawbacks here:
- Lack of Security: Basic authentication is susceptible to several types of attacks, such as man-in-the-middle attacks, packet sniffing, and replay attacks. Passwords are sent in clear text, making them vulnerable to interception, and there is no way to verify the identity of the client.
- Limited Password Management: Basic authentication does not offer features such as password expiration, account lockout, or password complexity requirements, which are essential for maintaining a secure authentication system.
- No Auditing Capabilities: Basic authentication does not provide any auditing capabilities, making it difficult to track and monitor authentication attempts and detect potential security breaches.
- Compliance Issues: Many regulatory standards, such as PCI DSS and HIPAA, require stronger authentication mechanisms than basic authentication, so relying solely on basic authentication can put organizations at risk of non-compliance.
Overall, while basic authentication is easy to implement and use, its lack of security features and limited functionality make it unsuitable for many modern applications and environments.
Why is passwordless authentication more secure than MFA?
According to a study by Verizon, 80% of cyber attacks are password related—making passwords one of the most easily compromised elements in your environment. With Passwordless Authentication, users don’t need to worry about password theft or data breaches that result from password compromises because passwords are no longer part of the equation.
Another question you may be asking yourself is, “I already have MFA enabled for all my users, how is Passwordless Authentication more mature?” Since MFA is an additional step to log in on top of passwords, it still relies on a traditional password that could be compromised. For example, if a hacker can guess a user’s password, a portion of their work is already completed which in return leaves a big portion of security relying on MFA. However, using Passwordless Authentication removes that reliance entirely.
The crucial prerequisite for you to enable Passwordless Authentication in your environment is to ensure that you have the correct licensing. If you have Azure AD Premium 1 and/or Azure AD Premium 2, you will have the ability to enable Passwordless Authentication in your environment. In the example listed below, our client had Business Premium licensing which includes Azure AD Premium 1. Our engineers at Rutter Networking Technologies were able to enable Passwordless Authentication for their environment.
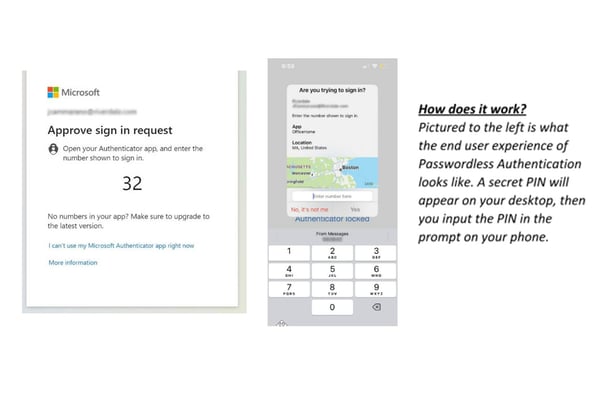
What impact does passwordless authentication have on the effectiveness of Zero Trust?
Prior to a shift towards a hybrid workforce, firewalls and VPNs were the main security solutions that every company went to first. These methods worked well within office walls; however, VPNs and firewalls are a perimeter-based solution and do not translate well to a hybrid work environment. At Rutter Networking Technologies we’ve learned that Zero Trust starts with secure access, which is why we’ve been advocating more and more for Passwordless Authentication.
Enabling this access method empowers your users because it protects them against password theft but also provides a seamless user experience. As a whole, integrating a Zero Trust Model into your environment is the best way to protect and empower users that are still adjusting to the hybrid work model. Zero Trust institutes a “deny all until verified approach” for access to resources from both inside and outside office walls.
The concept of a Zero Trust Model can be overwhelming since it covers every area of your cloud environment. However, incorporating simpler concepts like Passwordless Authentication into your organization helps bring your organization one step closer to aligning with the recommended security model. Passwordless Authentication not only aligns your environment closer to a Zero Trust Model, it also enables your workforce to have the ability to work from anywhere since they wouldn’t have to memorize long, complex passwords or depend on their IT department to manually reset their passwords. By removing this dependency, it allows your users to be more productive while being able to verify user identity and strengthen your organization’s security posture.
At Rutter, we offer a range of solutions and services to help organizations protect themselves from digital threats. From employee training and awareness programs to advanced threat protection technologies, we have the expertise and experience to help you safeguard your organization. Don't let password related incidents compromise your organization's security and reputation or reduce your productivity. Contact us today.



Comments