
First, it was the simple things – up/down monitoring for the most critical firewalls and routers. Next, it proceeded to monitoring the switches and then the servers. Soon after, you had all the significant systems monitored so that nothing could be offline without notification. And everyone was happy.
But you knew there was more.
So, you began expanding the role of your monitoring environment to include SNMP data gathering for all those devices. These new capabilities could reveal how your systems were performing; not just when they were up or down. If a link was over-utilized, you could create a graph or table which articulated that and would identify when the issue started. If a server was running low on memory, you had that covered too. You even had the UPS and the HVAC system get into the game, so you had the pulse of the entire data center.
This was the status quo for a while, and it was sufficient for that time.
Nowadays, not only are there more systems to be managed, but applications and services are becoming a primary focus. Furthermore, all of them are sharing the same servers, switches, routers, and firewalls. Managing systems at this level requires a different approach and a different type of data – NetFlow!
What is NetFlow?
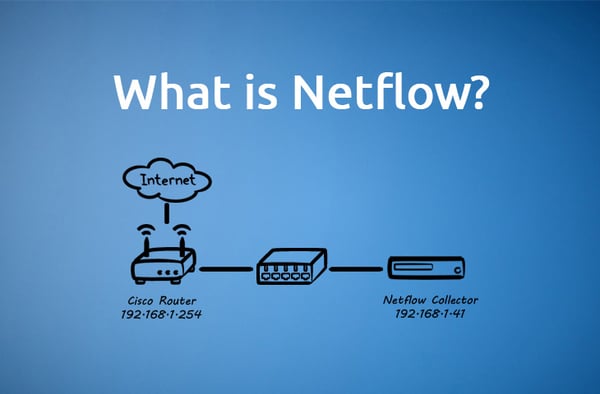
NetFlow is a router statistics protocol developed by Cisco that enables the collection of IP traffic information, so you can monitor your traffic and see who is using your bandwidth. More importantly, it helps you understand how that bandwidth is being used. NetFlow-enabled routers export traffic statistics as NetFlow records which are then collected by a NetFlow collector. The collector does the traffic analysis and presentation.
The protocol allows you to really drill down into your network traffic to see protocol, source, destination, and traffic volume. With this information, you can visualize traffic patterns throughout the entire network. This overarching view of traffic flow allows network operations and security operations teams to monitor when and how often users access an application in the network. Teams can use this data to facilitate the detection of potential security or policy violations.
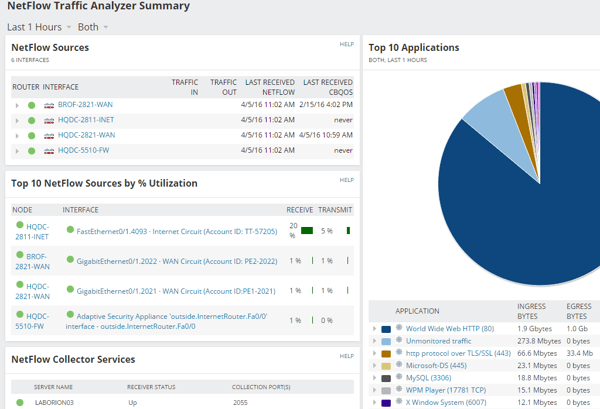
For those of you who don’t use Cisco equipment; not to worry, most vendors have their own version! For example, Juniper supports Jflow, Dell and NetGear use sFlow, and Riverbed uses CascadeFlow. VMware also supports export of NetFlow data from their Distributed Switches. Each of these are vendor-specific implementations of NetFlow. When choosing a NetFlow collector, be sure to check compatibility with your primary equipment vendor.
Now that you’ve acquired this new flow of information, you’re ready to gain a much more comprehensive insight of what your network is doing and who is doing it. Get yourself a good NetFlow collector, configure your network to deliver the NetFlow data, and dig into the real network stats.



Comments