Today, organizations are faced with the unique challenge of protecting critical assets and data from a more diverse and broad set of threats than ever before. Advanced malware and ransomware targeting the endpoint continues to evolve and morph at an incredibly fast rate.
Organizations of all sizes across all industries continue are being targeted and traditional signature-based technologies struggle to keep up with unknown threats. This trend is unlikely to change any time in the future.
Some important facts to keep in mind as you look to address this problem are that over half of the attacks in 2016 targeted companies with less than 1000 employees, phishing is still a huge problem globally and ransomware is on the rise at a rate that will continue to grow. Also attackers are not simply owning an environment and moving on. They can and will lurk for as long as it takes to gain valuable information (and in some cases that could be years).*
For a long time, as an industry, we have advocated for patching and strong anti-virus as ways to help mitigate these risk, but yet, the statistics and the news of continued incidents seem to further indicate that these are simply not enough.
At this point, it's safe to say that a protection strategy needs to include the ability to identify and prevent unknown threats before they can cause damage, which is why Rutter Networking Technologies has partnered with Crowdstrike.
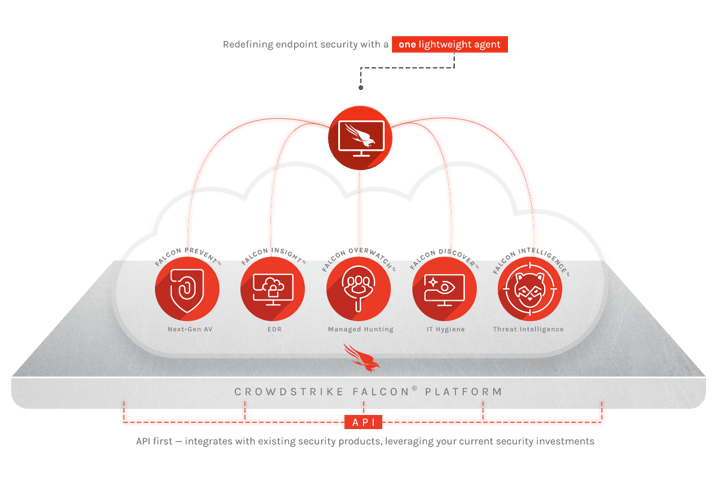
The ability to provide Next Generation Anti-Virus + Endpoint Detection and Response + Managed Threat Hunting in a single agent that is cloud managed significantly reduces the available attack surface that an attacker can leverage to be successful.
At this point, signature based technologies are not the right solution. File signatures can be changed in seconds with little to no effort, and modern malware is specifically programmed to evade even the most sophisticated signature-based technology, even some sandboxing and next-generation products can be fooled. But Crowdstrike’s multi-layered approach to protection is not so easily fooled.
Sometimes, different is better. Crowdstrike’s unique architecture provides a framework that is focused on preventing modern attacks and goes far beyond being just a point solution for a single problem.
To be successfully you need to leverage an architecture cable of allowing you to:
- See the big picture instead of focusing on point challenges, such as malware, and avoid being blind-sided by malware-free attacks
- Get the scalability, adaptability and speed required to defeat attackers' ever-changing tools and techniques
- Operationalize in hours and free your team from the treadmill of deployment, maintenance and updates
- Use people, process, technology and intelligence in concert for the most effective protection
You also need to move away from the traditional endpoint security pitfalls that simply are not effective.

Ultimately, the changing threat landscape requires that we as an industry look at new and innovated approaches to these problems. Many organizations have unfortunately learned this lesson the hard way.
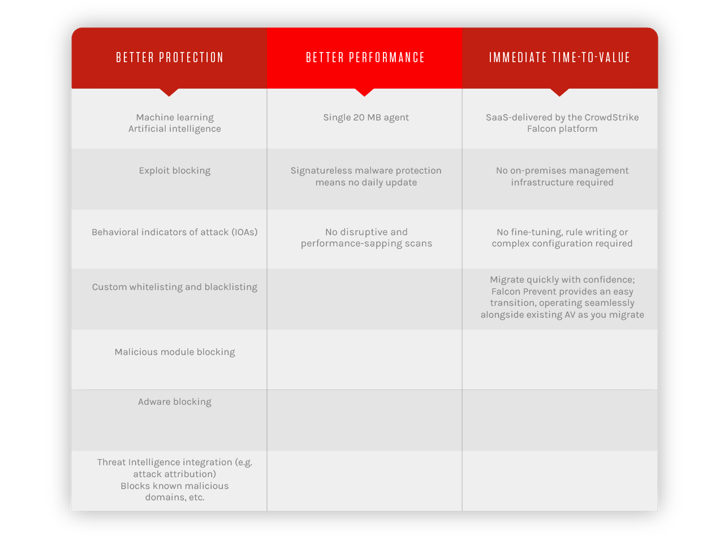
Crowdstrike security is able to provide better protection, better performance and an immediate time to value that is unmatched in the industry because of their approach to securing the endpoint.
It is important to understand what differentiates Crowdstrike services from other technologies.
- SaaS Delivered
- Single Agent
- Built from the ground up
- Real time visibility
- Integrated Threat Intelligence
- Streamlined Threat Defense
Rutter Networking Technologies, a certified Crowdstrike partner, will be hosting a webinar on October 17th at 10 AM, to delve further into these topics and discuss how you can better protect your organization from unknown threats including ransomware. Register for our upcoming webinar with Crowdstrike today.
*Data from 2016 Verizon Data Breach Report





Comments