
Once the decision has been made to stage an Active Directory site in a cloud tenant, there are some core principles which should be noted.
First, Active Directory is a product that was born before the cloud age. From a Kerberos perspective, the rules for Domain Controllers and workstations are not different that on-premise consumers.
Because of this the primary DNS available to servers and workstations alike should have key AD related zone information. Per this Microsoft article:

Without access to these records, a computer would be unable to find the nearest site, an available GC, etc.
Second, the primary DNS suffix search must always be the domain in which the computer belongs. The workstation must be able to resolve it and other domain members by the simple host name.
Using these core principles, Active Directory DNS zones must have primary availability from a lookup perspective. As seen in this AWS article, Domain Controllers are hosted in different availably zones to avoid cases like rack failure, etc. However, when a request takes place from a AD joined machine within the PVC, the request first goes to AD zone. From there is acceptable to establish forwarders to cloud dns for other lookups.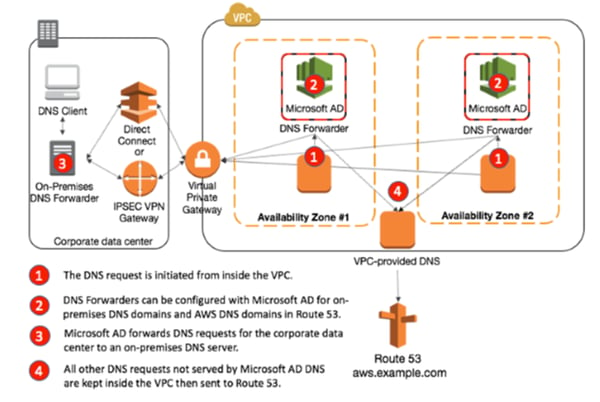
A few things to note:
- Ideally the zones should be AD integrated zones, that way any new forest related zone or reverse zone needed for AD can automatically be replicated to pertinent Domain Controllers within the ntds.dit file. For larger environments this is a reduction of overhead. It also simplifies the forwarding model in the cloud.
- When situating domain controllers in a cloud tenant, place for a site topology and replication. Without a clear definition of AD sites and subnets, AD consumers who resolve to cloud situated DNS zones, may attempt to contact on premise Domain Controllers for other services. This might result in latency or replication issues.
- Domain Controllers hosting AD zones should not be placed in the same rack. In the diagram above, you will note the separation by an availability zone. Both AWS and Azure offer availability zones in the event of loss of datacenter, that a comparable server within the region will remain online.
Active Directory still holds the vast market share for on premise authentication. With IaaS consumption accelerating, it more common to develop AD sites within a cloud tenant. As this article shows, that while AD is versatile, the product was developed and has no awareness of the cloud. For Kerberos consumption, it is imperative that all domain consumers in the cloud have the core DNS requirements in place to function.




Comments